I DELIBERATELY Infected my PC With Ransomware - How to Protect Against Ransomware?
In this piece, I want to talk about how to protect your files against ransomware. And yes, I deliberately infected my PC for that. I mean, what good is a theoretical article about ransomware protection if what it describes hasn’t been tested against real-world calamity scenarios, right?
Absolutely!
So here I am explaining my very simple experiment with ransomware to show you how you can defend your computer against ransomware attacks effectively.
Now, ransomware has been around for many many years and some incredibly advanced strains of ransomware viruses have emerged over the last few months. There’s an entire industry behind it and many governments and large corporations have fallen victim to ransomware attacks.
Even organizations that have very considerable resources at their disposal to invest in cyber security and ransomware protection have featured in headlines about ransomware attacks.
With that in mind, you may ask yourself how a simple individual like me can say with confidence that I know how to protect against ransomware attacks effectively. Let’s face it: ransomware is a million dollar industry where some very smart and very talented individuals have spent decades perfecting their impressive arsenal of malicious software code.
And I’m not the smartest person in the world.
Heck, I’m usually not even the smartest person in the room. But I’ve always been very passionate about the things I did. And I found confidence in the method I use to protect against ransomware. Because it’s so simple. That will become clear further on.
My Ransomware Protection Story
I had been thinking many times about how to protect against ransomware since my first encounter with it in 2012. A customer of mine got hit and all their files were encrypted. They came to me with the request to try and recover their encrypted files and to implement a strategy to protect their network against future ransomware attacks.
After a little investigation I was relatively quickly able to decrypt their files (all of them) by using a ransomware decryption tool. The idea of these tools is that you feed them two versions of the same file: one file that has been encrypted by the ransomware virus and in addition to that also an unencrypted (original) version of the file. The tool then calculates the encryption key that was used to encrypt the file by comparing the two files. Once the encryption key was calculated, I could use the key to decrypt all other files of my customer.
Obviously this method only works if you still have at least one original (unencrypted) version of a decrypted file available somewhere.
And if you live in 2012.
Fast forward to today, ransomware has become A LOT more sophisticated. For 75 bucks you can buy your own ransomware DIY toolkit online and you can start wreaking havoc on as many systems as you can get your hands on using an encryption technology that no decryption toolkit in the world is capable of cracking open.
And those are only the script kiddies ransomware incarnations.
So how do you protect ransomware from locking your pc in modern times? I’m glad you asked! Let’s continue.
Ransomware Protection and Backups
Since that first hit with my customer in 2012 I’ve had several other small business owners who approached me for help because they had been attacked with a ransomware virus. It may start to sound like I’m specializing in this stuff, but I’m not.
What I do know though is this: every time computer security experts come up with a new strategy to defend against ransomware, cyber criminals come up with an answer.
To give an example, as ransomware attacks evolved and started attacking backups as well, we saw ransomware defence products making their entrance in the backup software market. Macrium Reflect backup software has introduced “Image Guardian” and Acronis has real-time protection to stop malicious activity, just to name a few.
This sounds promising, but there can still be vulnerabilities. If you don’t keep your backup software rigorously updated, you’re still at risk. I have been involved with a client who had their Macrium Reflect backup encrypted by ransomware, even though they had Image Guardian set up. Of course, if the backup software isn’t kept up to date, you shouldn’t be surprised that the system is still vulnerable.
We all understand that not all (backup) software is kept up to date to the very latest version.
But it has had me thinking about how to protect against ransomware many times. The conclusion is that you can spend an enormous amount of resources to protect against ransomware viruses but you still need to be prepared in case it hits you anyway.
In fact, making sure that you are prepared in case a ransomware attack hits you is much simpler than you might think.
So let’s see how to protect against ransomware in Windows 10 with a simple strategy that will protect your files no matter what.
How to Protect Against Ransomware: Air-Gapped Backup
An “air-gapped” backup is a backup that has no connection to any computer whatsoever. It’s also a sophisticated way of saying that your external hard drive containing your backup is laying on the shelf. If it’s not connected, there is no way that a ransomware virus can access it.

If you rotate your backups between two or more backup devices and you keep one of them disconnected from your computer, your backup will always be protected against ransomware. No ransomware will ever be able to attack your external hard disk if that disk isn’t connected to your computer, no matter how sophisticated it is.
For normal home use, a backup to an external hard drive is a good way to protect your files from catastrophic events such as ransomware. If you can now switch this external hard drive periodically with another one and always have one drive disconnected, you’ll always have a reliable, unaffected backup available.
Of course this doesn’t mean that you shouldn’t protect your Windows 10 computer against ransomware attack using best practices (keep Windows up to date, use Windows Defender or an antivirus program) but if you do get hit despite these precautions you’ll be back up and running very quickly. And you won’t have to pay a penny to get your files back because you will be able to restore them.
Let’s see how easily this would work out in a real-world example.
As mentioned in the introduction, I even went as far as deliberately infecting a computer with ransomware just to be able to show the process.
As soon as the ransomware had finished its job of encrypting my files, my computer was locked and I got the ransomware message on my screen:
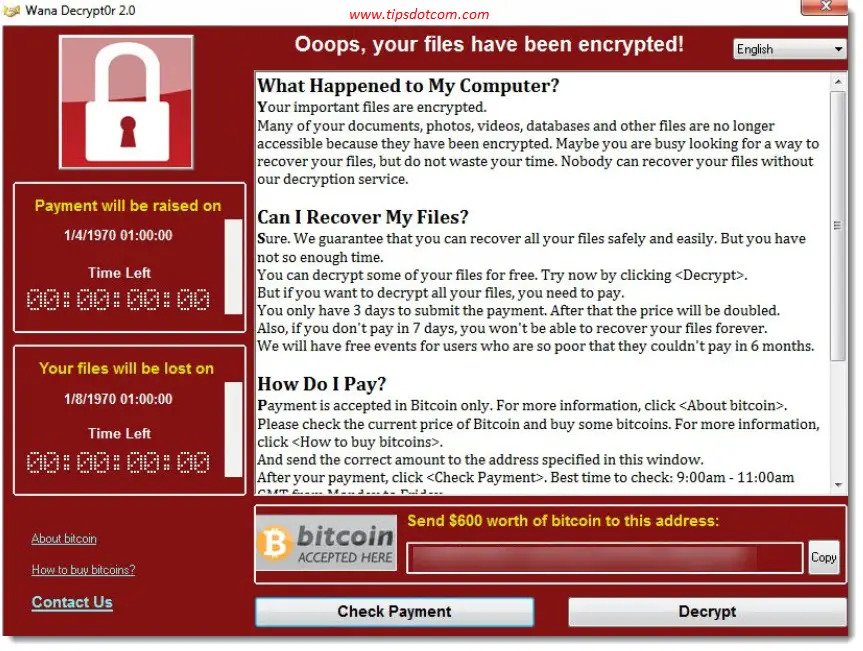
Time to insert my Macrium Reflect rescue media and shut down the computer. I then hooked up my external hard drive containing my valid backup and booted the computer from the Macrium Reflect rescue media. Please note that it’s very important to only connect your hard drive with your backup files after you’ve started your computer from the rescue media. If you connect it before that, the ransomware may (and probably will) attack your backup files as well.
I was greeted by the Macrium Reflect opening screen:
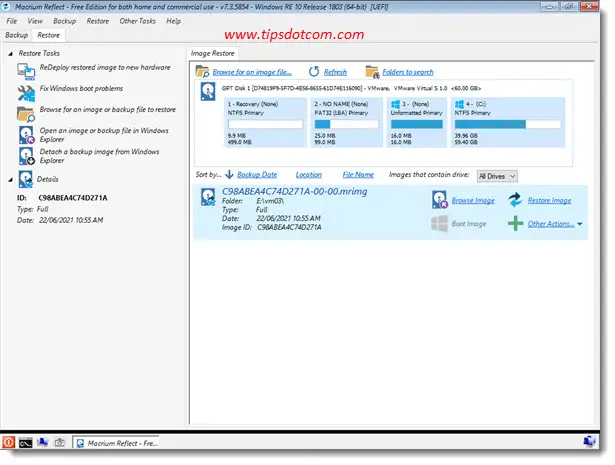
I then selected my backup file and clicked the “Restore image” button.
Moving forward I verified the source and destination drives in the restore wizard ...
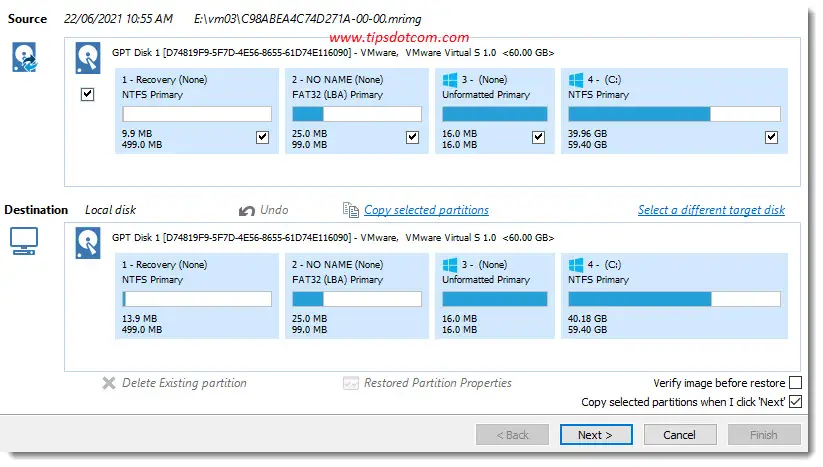
... and let the Macrium Reflect restore wizard do its magic.
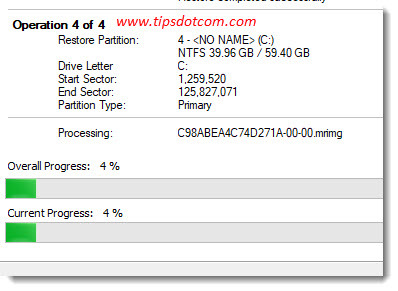
After a few moments, the restore was successfully completed and I could restart my computer.
Because the infected hard drive partitions are overwritten by the restore process there is no more sign of ransomware to be found after the restore. All files are intact as well.
That’s it, it shouldn’t be more complicated than that to keep your files safe.
Creating an air-gapped backup available really isn’t all that complicated and will give you peace of mind that your files will be protected, no matter what kind of virus hits you. All you need is a set of at least two external hard drives for your backups and backup software.
You can check my article on how to choose an external hard drive for your backups if you’re not sure which one to use.
As far as backup software is concerned, you can use the built-in Windows 10 backup functionality, which will do perfectly fine. Personally, I like to use Macrium Reflect because the built-in Windows 10 image backup doesn’t support individual file recoveries (and because Macrium Reflect is pretty easy to use and has a bunch of nice features).
It has a free version for non-commercial use that works fine for what you need. On top of that, it offers native support for a disk-rotating schema like the one I explained above, which is a plus for me!
I know I mentioned a case above where Macrium Backup’s “Image Guardian” was activated and the backup was still encrypted, but there are two reasons why that doesn’t stop me from using the product. First of all, the Macrium Reflect software wasn’t kept adequately updated in that particular case, which makes it vulnerable. In addition to that, as long as you keep at least one of your backup devices disconnected from your pc, you are sure that no ransomware (or other malware) can access it. No matter whether your plugged in backup device was attacked or not.
But What About Online Backup Services?
Yes, there are online cloud backup services that you can use and I’m not saying that they are no good. All I’m saying is that you can pick up two (or more if you please) external backup devices that aren’t expensive to buy and if you make sure that one of them is kept in a safe place, disconnected from your computer, you have a 100% chance of success in keeping your files safe. It doesn’t get much easier (and cheaper) than that.
I mean, if you count the monthly cost of storing your backups in the cloud or the license cost of the most advanced backup software, it all adds up. Plus, if you store your backups on a NAS device or anything else that’s connected to your system, how will you ever be able to have peace of mind that no ransomware will ever be able to attack your backups? If your backup software can access the device to store your backup data, that means that there is a possibility that some ransomware will find a breach and attack your backup.
If you put your backup device in a drawer, there is no way that that can happen.
If you've enjoyed this article or found it useful, I'd appreciate it if you'd let me know by clicking the Like (or Share) button below. Thank you!
New! Comments
Have your say about what you just read! Leave me a comment in the box below.